Metadata Enumeration with FOCA
One very important part of any pentest is the gathering of information of the target network that will be attack and on area that is gaining a lot of traction is the enumeration thru metadata. A tool I recently learned about by listening to the great podcast Exotic Liability where they mentioned the FOCA tool by Informatica64 when talking about their presentation at Blackhat Europe 09 you can either download the FOCA tool or you can use the webpage to summit your document for analysis. I do prefer to do most of my analysis locally since on almost all pentests I have conducted all information is confidential and the sharing of information with third parties is not permitted . This tool will analyze metadata from Microsoft Office Documents, PDF files, Open Office Files and Word Perfect files, EXIF Metadata out of images and the best part is that you can add the files you collected manually or found and downloaded thru web searches using Google and Live Search witch makes it extremely flexible for pentests. it will enumerate Users, Folders, Printers, Emails and the version of Software used to create the file. This tool will run on Windows XP and Windows Vista, I found it to be really unstable in Windows 7 Beta.
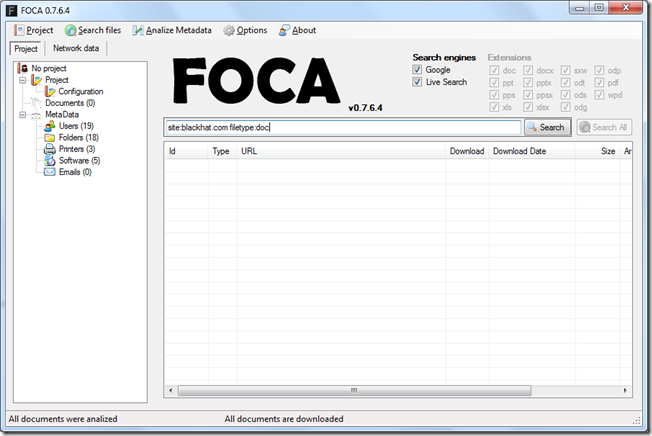
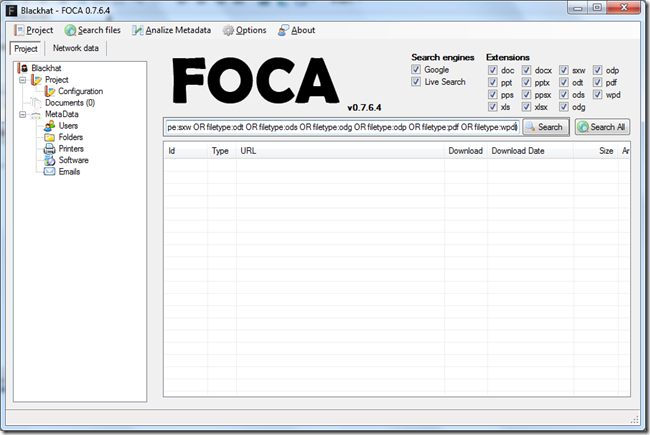
After downloading run the setup executable and the tool will be available in the start menu under programs. Once you execute the application you should see a screen line this one:
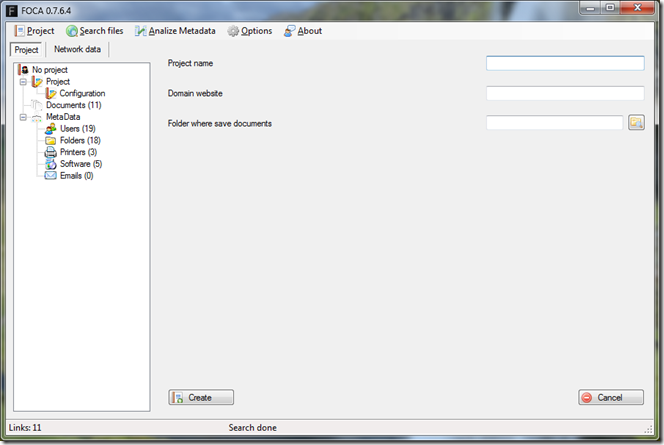
You can press Project –> New Project and start a new project where you give the Project Name, the Website to enumerate for documents and a give it a place to download and store the documents.
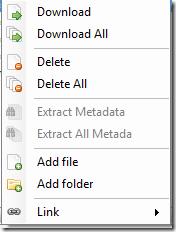
You can also instead choose to add a single file or folder of files that you have gathered previously via email, social engineering or any other way by Righ-Clicking with the mouse on the document list area and choose either the Add File or Add Folder option.
When you select to create a New Project you the screen will change in the following manner giving you the option of which files to download and what search engine to use.
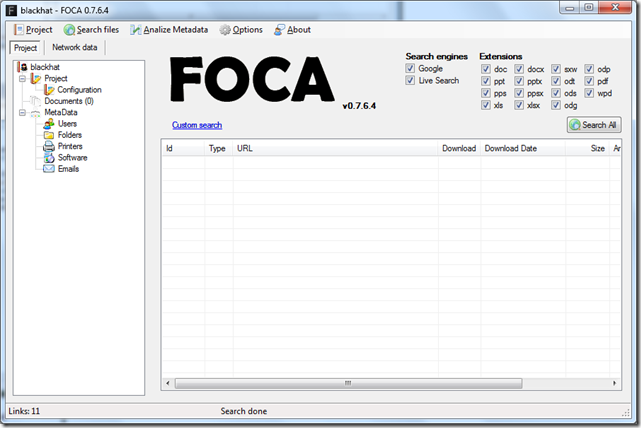
But what if the file type you are looking for is not in the options like PNG or JPG? you can click on the Custom Search link and enter the Google query your self or add filetype:<extension> like it is shown in the image below.
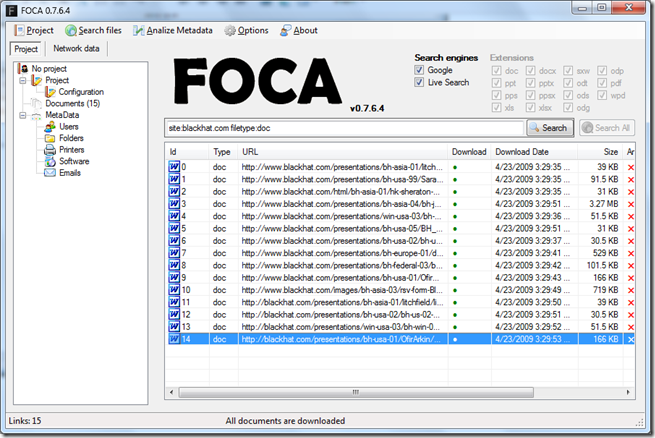
For the following screenshots I will enumerate and download only doc files from Blackhat.com, so I hit search and you can see the files that where found, one it has finish you can righ click and download only specific files of choose to download them all. Once Downloaded you can righ-click again on them and choose to extract the metadata of a single file or select to extract the metadata of all the files.
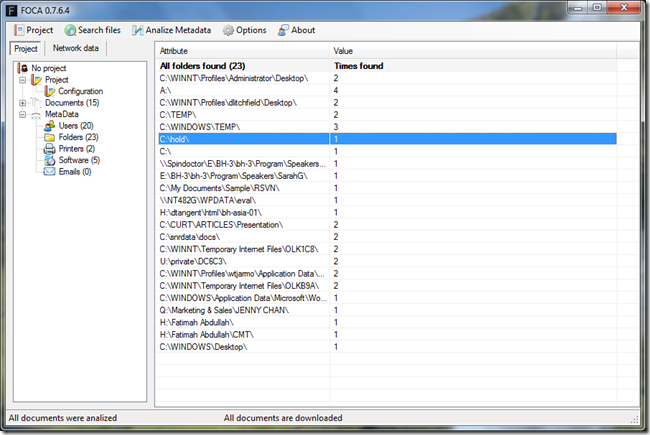
Once it has finished extracting all the metadata you can look at it by clicking on the type or go to Documents select the document and click on it to get even more information not classified in the types given like EXIF data. Here I clicked on the folder tab and you can see I can identify usernames, location, servers and paths on the network of where this documents where created and stored, on some I have tested I was even able to enumerate Sharepoint Server structures.
This information can be exported in to a text file by right-clicking on the attribute and choosing to export data to a file, this can later be used to feed the data in to other tools or to gain information for further attacks like finding types of printers that can be used to store files or exploit since embedded device security tends to be low, or attack shares by dropping office documents with Meterpreter VBA shells or setting autirun.ini files to launch payloads or exploits on client PC’s, The options are many.
I will definitely be adding this tool to my toolbox and making it part of my methodology when executing target enumeration during pentetst. I hope you find this information useful and special thanks to the Exotic Liability team for mentioning this tool.