Introduction to WMI Basics with PowerShell Part 1 (What it is and exploring it with a GUI)
For a while I have been posting several ways I use WMI (Windows Management Instrumentation) in my day to day and in consulting but have never covered the basics. Talking with other people in the security field and in the system administration worlds they seem to see WMI as this voodoo black magic that only a few who venture in to it master it. Do to the programmatic way that one retrieves information from it I see why some who have not coded or scripted may be afraid of it, so I will take my best attempt at showing the basics of it in a simple easy to understand way.
What is WMI?
WMI is the Microsoft implementation of Web-Based Enterprise Management (WBEM), with some enhancements in the initial version of it, WBEM is a industry initiative to develop a standard technology for accessing management information in an enterprise environment that covers not only Windows but also many other types of devices like routers, switches, storage arrays …etc. WMI uses the Common Information Model (CIM) industry standard to represent systems, applications, networks, devices, and other managed components. CIM is developed and maintained by the Distributed Management Task Force (DMTF).
All of that sounds pretty but when Microsoft developed the first versions of WMI they use DCOM (Distributed Component Object Model) wish if a proprietary Microsoft Technology, so the standards and cross compatibility just took a back seat at the time, on more recent versions of the operating system with Windows Management Framework 2.0 and above MS started to include more and more of the standards and shifter to using WS-Management SOAP-based protocol thru their WinRM (Windows Remote Management) protocol.
We can look at WMI as a collection of objects that provide access to different parts of the operating system, just like with PowerShell objects we have properties, methods and events for each. Each of these objects are defined by what is called MOF (Manage Object Format) files that are saved in %windir%\System32\wbem with the extension of .mof. The MOF files get loaded by what is called a Provider, when the Provider is registered he loads the definitions of the objects in to the current WMI Namespace. The Namespace can be seen a file system structure that organizes the objects on function, inside of each namespace the objects are just like in PowerShell in what is called Class Instances and each of this is populated with the OS and Application information as the system runs so we always have the latest information in this classes.
Namespaces are organize in a hierarchical way where \root is the top level for all other namespaces. The default namespace where most of the other namespaces and classes are located is root\CIMv2 on Windows Kernel 6.x on Kernel 5.x it is Default\CIMv2. Some are installed by default and others are only available when specific applications are installed.
In summary each Namespace contains Classes, these have:
- Methods Actions that can be taken.
- Properties Information that can be retrieved.
- Instances Instances of the class objects (services, Processes, Disks) each instance with Methods and Properties.
- Events are actions that WMI can monitor for and take action when they happen.
Caveats of WMI
Now WMI is great, do not get me wrong, but sadly it does have some caveats the main ones being:
- Not all classes are available on all versions of Windows. Check
- Some applications even from MS have Providers in one version and not in another (Office) and in some cases they even change the properties and methods.
In other words if you plan on running WMI queries against a series of hosts that may be of different versions of Windows or a specific application do make sure you test and validate your results. This goes the same for Architecture if you are testing x64 or x86.
Exploring WMI with a GUI
There are currently several GUI tools out there that can be use to explorer WMI so once can decide what class, instance (object) or event one wants to work with. For many administrators one of the favorite tools to explore WMI has been the standalone WMIExplorer.exe from SAPIENs http://www.sapien.com
Microsoft updated to 1.1 their WMI Administrative Tools http://www.microsoft.com/en-us/download/details.aspx?id=24045
Microsofts Scripting Guy WMIExplorer.ps1 http://gallery.technet.microsoft.com/scriptcenter/89c759b7-20b4-49e8-98a8-3c8fbdb2dd69
All tools provide a GUI way to explorer WMI but they tend to have some issues in common:
- They tend to be slow since they parse all classes and namespaces when exploring
- Filtering for information is not the best.
Each tool has it’s advantages and disadvantages my to favorites that I keep using time and time again is the Scripting Guy WMIExplorer.ps1 and the one from Sapiens, the Sapies the main differences is that that one is a binary and the other is in PowerShell, also the PowerShell one allow me to see help information about the class that the Sapiens tool does not, in the Sapiens tool I have to go to MSDN and read the WMI reference documentation http://msdn.microsoft.com/en-us/library/windows/desktop/aa394582(v=vs.85).aspx
Since this will be a series on using WMI in PowerShell I recommend you go with the PowerShell one first. To get up and running with it we start by selecting the code for the script and saving it as WMIExplorer.ps1
Since this is a script and more than likely we do not have a code signing certificate to sign it we must change out execution policy to allow the running of locally created scripts. We do this using the Set-ExecutionPolicy cmdlet from a PowerShell session that is running as Administrator. The command would be:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser -Force
In the example command above I’m setting it only for the current user (No need to allow other accounts to run scripts without signing) and I give it the parameter of force so as to execute it without letting the system ask me if I’m sure I want to enable it.
Once saved and the policy has been set we can execute the script from a console or from ISE, I recommend that you run it as a background job so it will not lock your current session this is done using the Start-Job cmdlet:
Start-Job -FilePath .\WMIExplorer.ps1
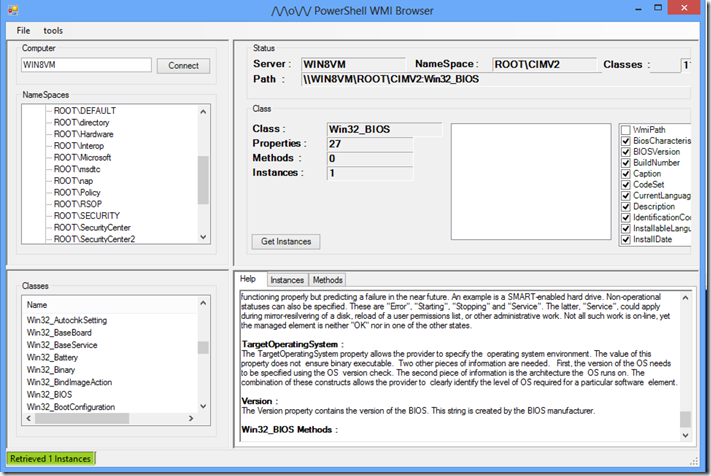
When the job is created you should be greeted by the following screen after a couple of seconds:
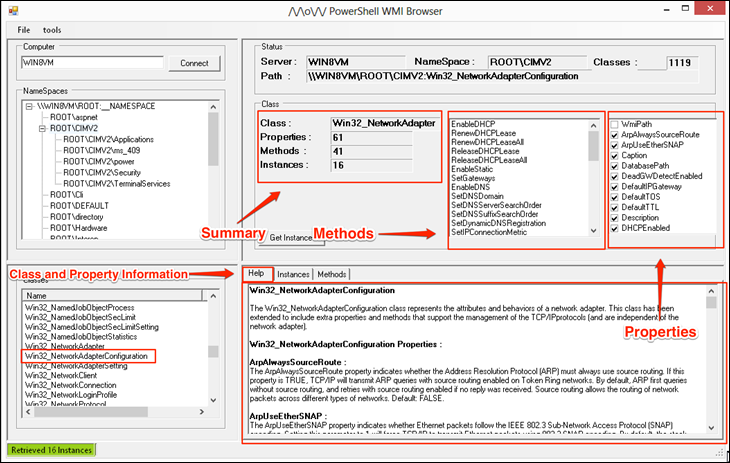
Do make sure you click on connect so it will start populating the information. When a class is selected detailed information about the class is populated so as to make it easier to identify what piece of information we want depending on what we want to do with class or instance of the class, the Help section will contain the information about the class and the definitions of the properties so as to know what each of those return.
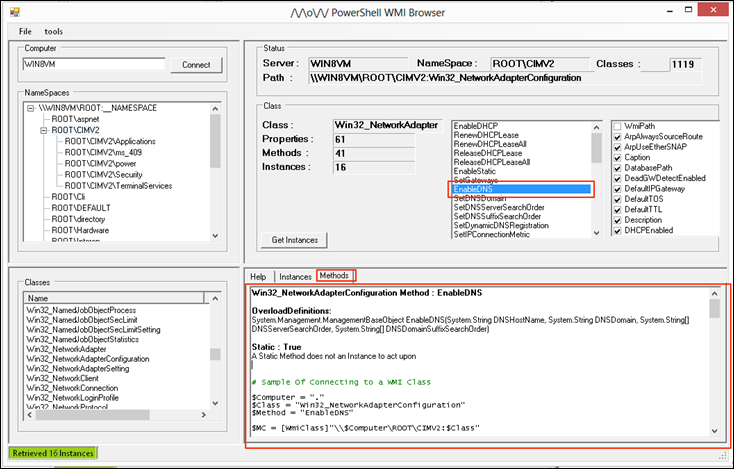
When we select a method of the class you will be able to see what information the method provides and even see examples of use of the method.
You will notice that there are several classes available that we can pull information from, many of these start either with CIM or Win32 and have the same name at the end. The difference between these classes is that one uses the Common Information Model schema and the Win32 classes are called Win32 Enhanced classes, in other words they leverage the Win32 API for information, My personal recommendation when you see both use the Win32 one.
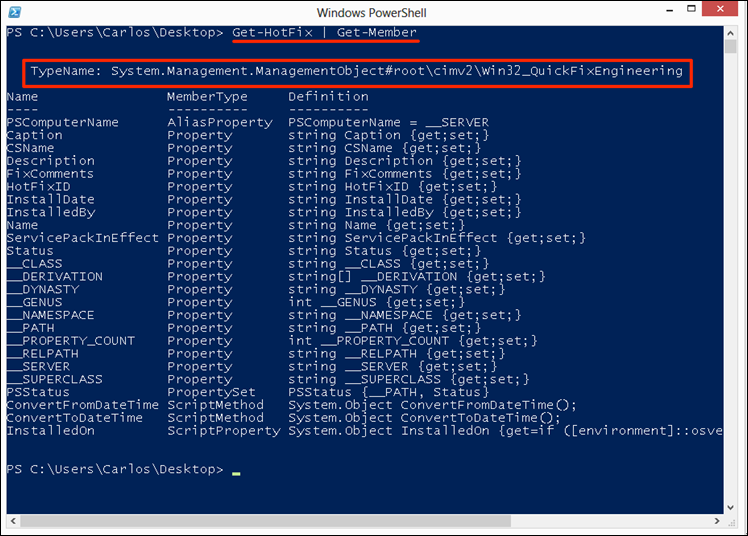
PowerShell uses WMI under hood quite a bit for many of it’s cmdlets. One good example is the Get-Hotfix cmdlet, if we look at the type we can see that it is returning a WMI object:
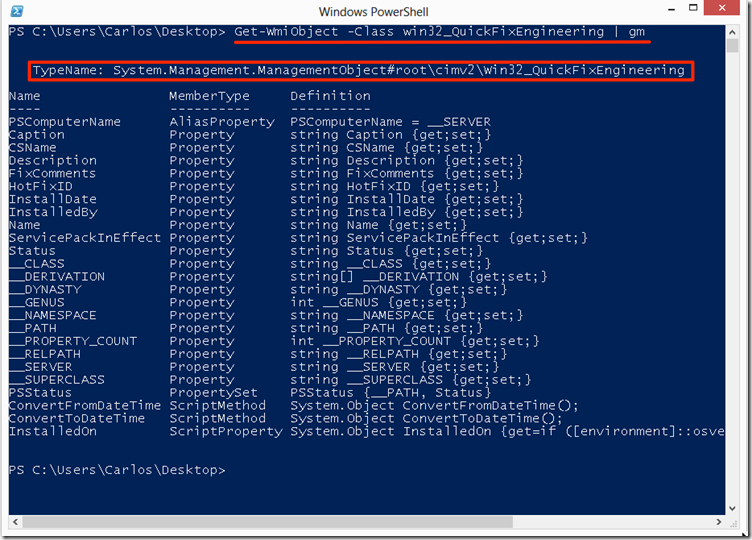
As we can see in the TypeName it is referencing System.Management.ManagementObject (same as WMI in .Net) and it is in the NameSpace root\cimv2 and the class name is win32_QuickFixEngineering if we do a query using the Get-WMIobject cmdlet we would get the same type:
On the net blogpost in the series we will go into how to navigate WMI with both the WMI and CIM cmdlets.
As always I hope you have found this information useful.