Microsoft EMET
Many times we are faced with the situation of not being able to patch software in time and many times do to the way companies work and handle security vulnerabilities the time of exposure is a very long one. Microsoft has worked in to making it harder for attacker to exploit code by adding in to the operating system and to several of their products mitigating technologies, but sadly not all Microsoft products or third party products use these mitigating technologies. To help with this Microsoft released the Enhanced Mitigation Experience Toolkit. This toolkit include several pseudo mitigation technologies aimed at disrupting current exploit techniques, it is not a perfect solution in terms that it can make it harder for known techniques used out there, so this makes this toolkit very effective in managing risk. It provides 7 protections:
Structure Exception Handler Overwrite Protection (SEHOP)
- Dynamice Data Execution Prevention (DEP) Application Level
- Dynamice Data Execution Prevention (DEP) System Level
- Heapspray Allocations
- Null Page Allocation
- Mandatory Address Space Layout Randomization (ASLR)
- Export Address Table Access Filtering (EAF)
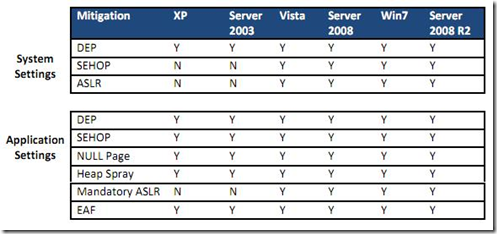
This options are not present on all Operation Systems
Also depends on the CPU
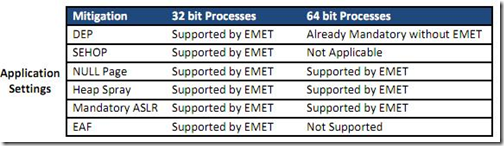
As it can be be seen from the table, the latest the OS the more protection can be used. The advantage of EMET is that many applications have to be compiled with proper flags and libraries to be able to use these protections, but with EMET they can be forced at the system and application level. With attackers moving more and more to client side attacks and with many companies dependent on applications that many times can not be updated do to the vendor not supporting them on newer versions of Windows, patches taking to much time or just plain quality problems from the company that programed the tool.
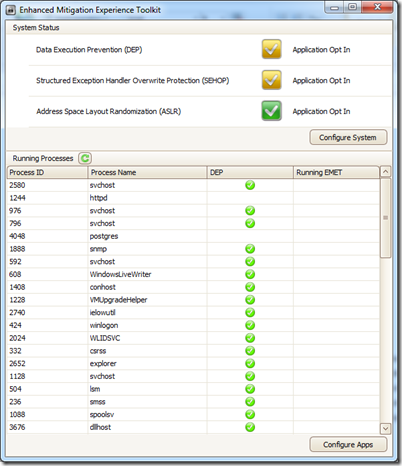
Once you install the tool the main screen is very Spartan in terms of information given:
You can see 2 configuration areas the top part for configuring the system settings and the lower part for configuring the application protection settings. The System configuration
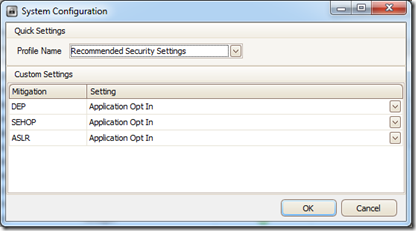
You can select one of 2 recommended profiles:
- Maximum Security
- Recommended Security Settings
or you can set each of the protection settings.
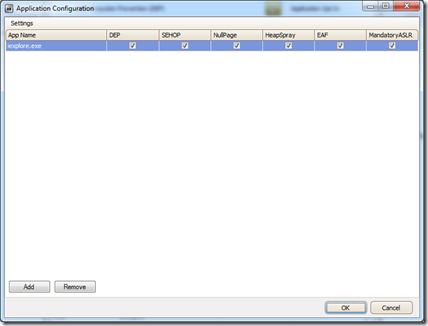
You can also configure several protections per application:
You can push the tool to your servers and client systems thru any package manager that can automate the installation thru MSI. The configuration of the programs to add for protection can be automated very easily via the command line:
C:\Program Files (x86)\EMET>EMET_Conf.exeUsage: EMET_Conf.exe [--list | --add path\program.exe | --delete path\program.exe | --delete_all]
I highly recommend this tools for anyone that run Microsoft Windows. I highly recomend it for all web browsers, Document editors , media player and for any service that can be touched via the network. I have test a large number of Metasploit exploits and found that this Microsoft solution has bloqued all exploits I could throw at my test machine, machines that I was able to compromise with each before I installed and configured EMET. I do hope MS integrates this in to Service Packs and on the next versions of Windows.
Download at: