About 2 months ago I was chatting with some of the members of one of the QA Teams at work and they where telling me about their workflows for automating the testing of code and hosts added to the lab. One showed me some of the scripts they use and then it came to me why not automate Nessus from with in PowerShell. I would say that in 2 days in my spare time using Brandon Perry Nessus-Sharp library for Nessus-XMLRPC written in C# https://github.com/brandonprry/nessus-sharp I forked the library and started modifying it to the needs I had I came up with a basic usable module. Sadly I got distracted with several projects and helping a bit to organize BSides PR I had not updated and cleaned the code until recently. Now that I have more time I would like to share the function I created and merge in to Posh-SecMod PowerShell module since I believe they could be useful to someone as they have to me.
Installing the Module
Posh-SecMod can be found at
https://github.com/darkoperator/Posh-SecMod and installing it is very simple. The module is a PowerShell v3 module only at the moment so it will only run on:
- Windows 7
- Windows 2008
- Windows 2008R2
- Windows 8
- Windows 2012
For installing PowerShell on versions of Windows bellow you will need to install .Net 4.0 and then download and install the Windows Management Framework 3.0. Believe me it is all worth it just for the ISEv3.
We start by running PowerShell with elevated privileges and make sure that you have set the ExecutionPolicy to RemoteSigned since none of the scripts, binaries and modules are signed with authenticode.
Set-ExecutionPolicy RemoteSigned
We then install the latest version of PSGet from inside PowerShell:
(new-object Net.WebClient).DownloadString("http://psget.net/GetPsGet.ps1") | iexOnce installed we can either install directly from GitHub using PSGet to Download the latest version of the module zip from GitHub by running.
import-module PsGet
install-module -ModuleUrl https://github.com/darkoperator/Posh-SecMod/archive/master.zip
The module will be available for use.
Listing Function to Interact with Nessus Server
To get a list of all the functions available for managing and automating Nessus we can load the module and filter the list for the word Nessus:
C:\> import-module Posh-SecMod
C:\> Get-Command -Module Posh-SecMod | where {$_.Name -like "*nessus*"}CommandType Name ModuleName
----------- ---- ----------
Function Copy-NessusPolicy Posh-SecMod
Function Get-NessusPolicyXML Posh-SecMod
Function Get-NessusReportHostKB Posh-SecMod
Function Get-NessusReportHostsDetailed Posh-SecMod
Function Get-NessusReportHostSummary Posh-SecMod
Function Get-NessusReportItems Posh-SecMod
Function Get-NessusReportPluginAudit Posh-SecMod
Function Get-NessusReports Posh-SecMod
Function Get-NessusReportVulnSummary Posh-SecMod
Function Get-NessusServerAdvancesSettings Posh-SecMod
Function Get-NessusServerFeedInfo Posh-SecMod
Function Get-NessusServerGeneralSettings Posh-SecMod
Function Get-NessusServerLoad Posh-SecMod
Function Get-NessusServerMobileSettings Posh-SecMod
Function Get-NessusSession Posh-SecMod
Function Get-NessusUsers Posh-SecMod
Function Get-NessusV2ReportXML Posh-SecMod
Function Import-NessusV2Report Posh-SecMod
Function Invoke-NessusScan Posh-SecMod
Function Invoke-NessusScanTemplate Posh-SecMod
Function New-NessusScanTemplate Posh-SecMod
Function New-NessusSession Posh-SecMod
Function New-NessusUser Posh-SecMod
Function Remove-NessusPolicy Posh-SecMod
Function Remove-NessusScanTemplate Posh-SecMod
Function Remove-NessusSession Posh-SecMod
Function Remove-NessusUser Posh-SecMod
Function Resume-NessusScan Posh-SecMod
Function Show-NessusPolicy Posh-SecMod
Function Show-NessusScans Posh-SecMod
Function Show-NessusScanTemplate Posh-SecMod
Function Start-NessusServerFeedUpdate Posh-SecMod
Function Stop-NessusScan Posh-SecMod
Function Suspend-NessusScan Posh-SecMod
Function Update-NessusScanTemplate Posh-SecMod
Function Update-NessusUserPassword Posh-SecMod
Lets start by connecting to a Nessus Server. For this module I follow the philosophy of Session like we have with PSSession in PowerShell so as to be able to work with more than one Nessus server at the same time providing me greater flexibility. the Function to create a session is called New-NessusSession. All functions have help information that tells the user the purpose and all have examples of usage that can be read using the Get-Help cmdlet or it’s aliases man and help. To se the general information on the function we would do a
help <nessus function>
Full details can be seen by adding the –Full option or to only look at the usage example we can just use the –Example option.
Connecting to a Nessus Server and Working with Sessions
Lets connect to a Nessus Server using the New-NessusSession function giving it the host to connect to, the credentials and since I do not have valid SSL Certificate on my test Nessus Server I use the switch –IgnoreSSL so it will not validate the certificate:
C:\> New-NessusSession -ComputerName nessus.darkoperator.com -Credentials (Get-Credential) -IgnoreSSLcmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
User : carlos
IsAdmin : True
Index : 0
SessionState : Nessus.Data.NessusManagerSession
SessionManager : Nessus.Data.NessusManager
IdleTimeout : 30
ScannerBootTime : 4/11/2013 12:04:58 AM
PluginSet : 201302261815
LoaddedPluginSet : 201302261815
ServerUUID : fd14bd4c-27bc-7c35-0308-876409e7758d0b0d82169800a061
Token : bfeaa869adea6cc99de404c73caf3d60594d92376716e28a
MSP : True
ServerHost : nessus.darkoperator.com
As you create connections to Nessus servers the connections a re stored in to the global variable $Global:nessusconn as you can see information about the server is included with each session object. Each session is referenced by the Index value. In fact each session has a type of Nessus.Server.Session we can have several connection and to one one we just do the same as we did before, the session is added automatically.
C:\> New-NessusSession -ComputerName 192.168.1.230 -Credentials (Get-Credential) -IgnoreSSLcmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
User : carlos
IsAdmin : True
Index : 1
SessionState : Nessus.Data.NessusManagerSession
SessionManager : Nessus.Data.NessusManager
IdleTimeout : 30
ScannerBootTime : 4/11/2013 8:53:03 AM
PluginSet : 201304120815
LoaddedPluginSet : 201304120815
ServerUUID : c1938596-19fe-dd76-9f74-1a680d6701b17b39b69cbe76805b
Token : 7275b221322838890ec4e50e9655591e49ce620c0c6fbb6f
MSP : True
ServerHost : 192.168.1.230
If you use a valid certificate on your Nessus Server you can skip the –IgnoreSSL. If the certificate is not valid you will see the errors as of to why it was not and you will see warning message asking you to continue. You can also use the –Verbose options, you will see that warnings and verbose messages come in different colors in PowerShell for easier distinction.
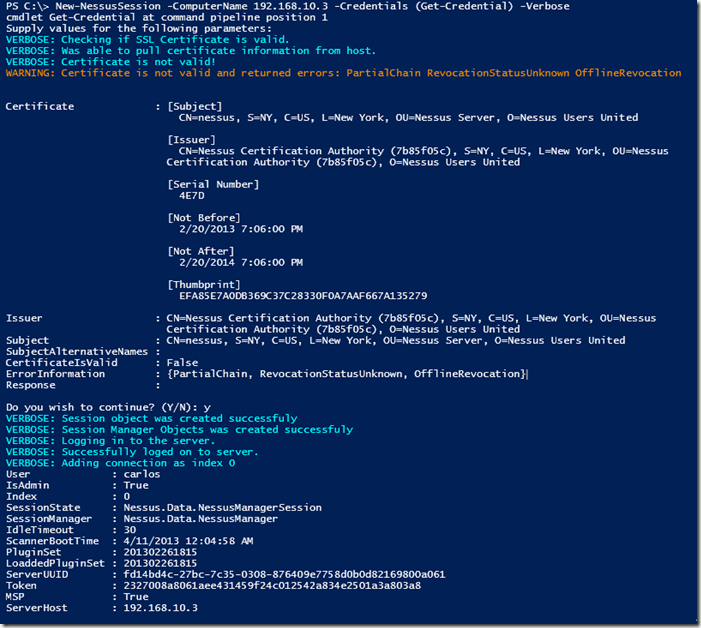
To get all current sessions we use the Get-NessusSession function and it also allows us to select an individual session and save it to a variable.
C:\> Get-NessusSession
User : carlos
IsAdmin : True
Index : 0
SessionState : Nessus.Data.NessusManagerSession
SessionManager : Nessus.Data.NessusManager
IdleTimeout : 30
ScannerBootTime : 4/11/2013 12:04:58 AM
PluginSet : 201302261815
LoaddedPluginSet : 201302261815
ServerUUID : fd14bd4c-27bc-7c35-0308-876409e7758d0b0d82169800a061
Token : bfeaa869adea6cc99de404c73caf3d60594d92376716e28a
MSP : True
ServerHost : nessus.darkoperator.com
User : carlos
IsAdmin : True
Index : 1
SessionState : Nessus.Data.NessusManagerSession
SessionManager : Nessus.Data.NessusManager
IdleTimeout : 30
ScannerBootTime : 4/11/2013 8:53:03 AM
PluginSet : 201304120815
LoaddedPluginSet : 201304120815
ServerUUID : c1938596-19fe-dd76-9f74-1a680d6701b17b39b69cbe76805b
Token : 7275b221322838890ec4e50e9655591e49ce620c0c6fbb6f
MSP : True
ServerHost : 192.168.1.230
To remove a session from the list and log off from the server we use the Remove-NessusSession function:
PS C:\> Remove-NessusSession -Index 0
True
Retrieving Nessus Server Configuration Settings
We can get feed and version information for each session using the Get-NessusServerFeedInfo function, we can pipe the the sessions from Get-NessusSession objects in to it or specify the session or sessions thru the index parameter:
C:\> Get-NessusSession | Get-NessusServerFeedInfo
Feed : ProFeed
ServerVersion : 5.0.2
WebServerVersion : 4.0.31 (Build H20130328A)
MSP : False
Expiration : 9/19/2013 4:00:00 AM
ServerHost : nessus.darkoperator.com
Feed : ProFeed
ServerVersion : 5.0.2
WebServerVersion : 4.0.31 (Build H20130328A)
MSP : False
Expiration : 12/31/2013 5:00:00 AM
ServerHost : 192.168.1.230
We can see if we have a proxy configured to pull Nessus Feed, this is known in the Nessus GUI as the General Settings, the functions to get the configuration we use the Get-NessusServerGeneralSettings :
C:\> Get-NessusServerGeneralSettings -Index 1
proxy :
proxy_port :
proxy_username :
proxy_password :
user_agent :
custom_host :
we can pull the advanced settings from the servers with the Get-NessusServerAdvancesSettings and as you can see one of my servers runs in windows and the other runs on Linux.
C:\> Get-NessusSession | Get-NessusServerAdvancesSettings
allow_post_scan_editing : yes
auto_enable_dependencies : yes
auto_update : yes
auto_update_delay : 24
cgi_path : /cgi-bin:/scripts
checks_read_timeout : 5
disable_ntp : no
disable_xmlrpc : no
dumpfile : /opt/nessus/var/nessus/logs/nessusd.dump
global.max_hosts : 125
global.max_scans : 0
global.max_web_users : 1024
listen_address : 0.0.0.0
listen_port : 1241
log_whole_attack : no
logfile : /opt/nessus/var/nessus/logs/nessusd.messages
max_checks : 5
max_hosts : 30
nasl_log_type : normal
nasl_no_signature_check : no
non_simult_ports : 139, 445, 3389
optimize_test : yes
plugin_upload : yes
plugins_timeout : 320
port_range : default
purge_plugin_db : no
qdb_mem_usage : high
reduce_connections_on_congestion : no
report_crashes : yes
rules : /opt/nessus/etc/nessus/nessusd.rules
safe_checks : yes
silent_dependencies : yes
slice_network_addresses : no
ssl_cipher_list : strong
stop_scan_on_disconnect : no
stop_scan_on_hang : no
throttle_scan : yes
use_kernel_congestion_detection : no
www_logfile : /opt/nessus/var/nessus/logs/www_server.log
xmlrpc_idle_session_timeout : 30
xmlrpc_listen_port : 8834
allow_post_scan_editing : yes
auto_enable_dependencies : yes
auto_update : yes
auto_update_delay : 24
cgi_path : /cgi-bin:/scripts
checks_read_timeout : 5
disable_ntp : no
disable_xmlrpc : no
dumpfile : C:\Program Files\Tenable\Nessus\nessus\logs\nessusd.dump
global.max_scans : 0
global.max_web_users : 0
listen_address : 0.0.0.0
listen_port : 1241
log_whole_attack : no
logfile : C:\Program Files\Tenable\Nessus\nessus\logs\nessusd.messages
max_checks : 5
max_hosts : 100
nasl_log_type : normal
nasl_no_signature_check : no
non_simult_ports : 139, 445, 3389
optimize_test : yes
plugin_upload : yes
plugins_timeout : 320
port_range : default
purge_plugin_db : no
qdb_mem_usage : high
reduce_connections_on_congestion : no
report_crashes : yes
rules : C:\Program Files\Tenable\Nessus\conf\nessusd.rules
safe_checks : yes
silent_dependencies : yes
slice_network_addresses : no
ssl_cipher_list : strong
stop_scan_on_disconnect : no
stop_scan_on_hang : no
throttle_scan : yes
www_logfile : C:\Program Files\Tenable\Nessus\nessus\logs\www_server.log
xmlrpc_idle_session_timeout : 30
xmlrpc_listen_port : 8834
If I wan to see how many users, scans and just the general load on the server I can use the Get-NessusServerLoad to get this information, this can come useful if we see a server running slowly or we want to script to always use the server with the least load to launch our scans:
C:\> get-nessussession | Get-NessusServerLoad
ServerHost : nessus.darkoperator.com
Platform : LINUX
ScanCount : 0
SessionCount : 2
HostCount : 0
TCPSessionCount : 0
LoadAverage : 0.00
ServerHost : 192.168.1.230
Platform : WINDOWS
ScanCount : 0
SessionCount : 1
HostCount : 0
TCPSessionCount : 0
LoadAverage : 0.00
Working with Nessus Server Users
We can list and work with users in the Nessus Server, we can find all the Nessus Server user manipulation functions by searching for *nessususer* in the name of the functions in the module:
C:\> Get-Command -Module Posh-SecMod | where {$_.Name -like "*nessususer*"}CommandType Name ModuleName
----------- ---- ----------
Function Get-NessusUsers Posh-SecMod
Function New-NessusUser Posh-SecMod
Function Remove-NessusUser Posh-SecMod
Function Update-NessusUserPassword Posh-SecMod
As you can see we can list the users, create a new user, remove a user and change the password of a user (if we are Admin of course). Lets start by listing the users on the server:
C:\> New-NessusUser -IsAdmin -Credentials (Get-Credential) -Index 0cmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
ServerHost : nessus.darkoperator.com
Name : Paul
IsAdmin : True
LastLogging : 1/1/0001 12:00:00 AM
Session : Nessus.Server.Session
I can change the password for the user Paul:
C:\> Update-NessusUserPassword -Index 0 -Credentials (Get-Credential)cmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
ServerHost : nessus.darkoperator.com
Name : Paul
IsAdmin : True
LastLogging : 1/1/0001 12:00:00 AM
Session : Nessus.Server.Session
C:\> New-NessusSession -ComputerName nessus.darkoperator.com -Credentials (Get-Credential) -IgnoreSSL
cmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
User : Paul
IsAdmin : True
Index : 2
SessionState : Nessus.Data.NessusManagerSession
SessionManager : Nessus.Data.NessusManager
IdleTimeout : 30
ScannerBootTime : 4/11/2013 12:04:58 AM
PluginSet : 201302261815
LoaddedPluginSet : 201302261815
ServerUUID : fd14bd4c-27bc-7c35-0308-876409e7758d0b0d82169800a061
Token : ec1d58e6b2fd2db1da9788bc6a259cd318ca551cc140de93
MSP : True
ServerHost : nessus.darkoperator.com
Lets close the session we created for testing and remove the user Paul:
C:\> Remove-NessusSession -Index 2
TrueC:\> Remove-NessusUser -Index 0 -UserName Paul
True
C:\> Get-NessusUsers -Index 0
ServerHost : nessus.darkoperator.com
Name : carlos
IsAdmin : True
LastLogging : 4/12/2013 12:23:04 PM
Session : Nessus.Server.Session
ServerHost : nessus.darkoperator.com
Name : admin1
IsAdmin : True
LastLogging : 12/31/1969 8:00:00 PM
Session : Nessus.Server.Session
On the next blog post I will cover how to work with Policies and Scans. I do invite you to install it and start playing with it and the other functions in the module.
